Ransomware is the infamous "ransom virus": it infects computers, encrypts data and demands money to make them readable again
Ransomware infects computers, but increasingly smartphones and tablets as well, blocking their use or making their data inaccessible through powerful encryption systems. If you don't pay, you can say goodbye to your precious digital information.
It used to be "or your purse or your life", today "or your money or your files": the concept is similar. Hackers, or rather, the criminal organizations of the new era, have found a new ploy to get money out of users. But if before they were shooting in the heap, now they are increasingly targeting important people and companies who are able to pay even larger sums of money to pay the ransom and get their often vital information back. Ransomware is a growing phenomenon and authorities, as well as private entities, are joining forces to deal with it.
What is ransomware
They are viruses, nothing more than viruses that spread with the same strategies. A user opens a seemingly harmless email or pop-up, and falls into the phishing net landing on infected websites. Or he installs a malware convinced that it is a useful and safe program, or he suffers an attack and his computer, smartphone or tablet are not properly updated or protected by a solid antivirus. It's not breaking news, but in this case, instead of the usual information theft - which is already a huge damage in itself - there's device and/or information lockout. While the virus that steals personal data aims to remain anonymous in order to keep on hoarding sensitive data, ransomware immediately reveals its presence by means of a message because its purpose is to blackmail and pocket the loot as soon as possible, in the vast majority of cases in electronic money such as bitcoin. Those who don't pay immediately - usually within the first 48 or 72 hours - risk seeing the price to be paid increase.
A business worth billions
The first ransomware dates back to 1989 and was christened PC Cyborg because payments were directed to a fictitious "PC Cyborg Corporation". However, the phenomenon didn't take root at the time because the time was clearly not yet ripe. It surfaced in 2014, began to spread strongly in 2015 and is literally ramping up in 2016: many analysts have already dubbed it the year of ransomware. Just a few numbers are enough to understand how widespread the phenomenon is now. I cybercriminali sganciano la “bomba” e aspettano che l’infezione si diffonda per iniziare a chiedere il riscatto di circa 300 dollari prima di fornire l’antidoto per “guarire” dal blocco i file criptati, per lo più foto e documenti personali. I risultati? Oltre 718,500 utenti sono stati ricattati – secondo una ricerca condotta dal Kaspersky Lab – tra l’aprile del 2015 e il marzo del 2016: con un aumento vertiginoso pari al 550% rispetto allo stesso periodo del 2014-2015.
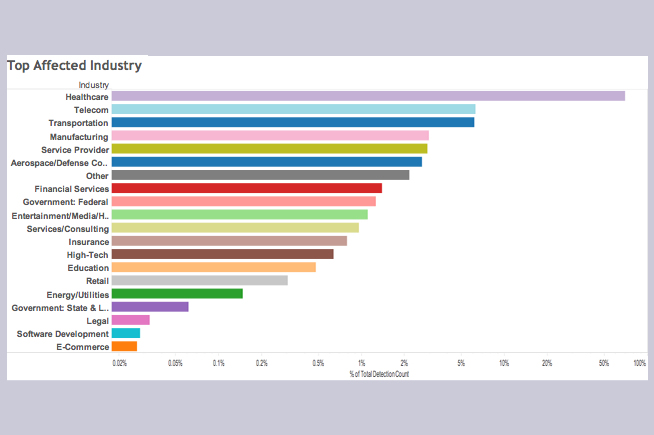 Fonte foto: Comunicato Stampa
Fonte foto: Comunicato Stampa
Rapporto FireEye
Era solo questione di tempo prima che, nella trappola del ransomware, cadessero anche le aziende. Qui non si tratta più delle foto delle vacanze o del cagnolino, ma di documenti finanziari se non addirittura delle cartelle cliniche dei pazienti! E le aziende, rispetto a un privato cittadino, hanno più risorse economiche e molto più da perdere. Ransom criminals, in short, are improving their aim. If an average ransom demanded from companies was, in 2015, about $ 680 - twice as much as the previous year - in 2016 - according to Symantec, it has certainly doubled. Another piece of data confirming that the phenomenon is booming comes from the FBI. The U.S. Federal Bureau of Investigation says it received 2,453 reports of ransomware infections in 2015 with losses of more than $1.6 million, up from 1,402 reports the year before. And the numbers are definitely on the rise in 2016. Ransomware, in short, is no longer a phenomenon to be underestimated. As evidenced by numerous initiatives aimed at dismantling it, such as the No More Ransom project, started by the Dutch national police - in collaboration with Europol, Intel Security and Kaspersky Lab - which today sees the adherence of 13 other countries, including Italy.
