Thousands of zombie computers ready for attack could be purchased for affordable amounts of money. The warning comes from security specialist RSA
Friday, October 21, was quite possibly the worst day for the Internet in a long time. A massive DDoS attack knocked out the DynDNS service, making sites like Twitter, Amazon and Skype unreachable for a few hours. The situation, however, could even get worse.
To launch the alarm is RSA, an American company expert in computer security, according to which in the deep web it would be possible to buy botnets (networks of PCs and connected devices remotely controlled by a single user) for a few thousand dollars (between 5,000 and 7,500 dollars). The news has been relaunched by Forbes magazine and the company has avoided revealing further details that could help identify the submerged platforms. Botnets, again referring to what RSA claims, can generate data traffic of up to 1 Terabit.
Why Botnets are Dangerous
If properly "remote-controlled," botnets (networks of computer devices infected with malware that allow you to take control of them remotely) have the potential to "shut down" the Net quite suddenly. If a sufficiently skilled hacker manages to get his hands on a network of zombie computers composed of tens of thousands of devices (smartphones, smartTVs, security cameras, computers and various appliances) he could set up very powerful attacks against any portal. La dimostrazione arriva, per l’appunto, dall’attacco di venerdì 21 ottobre, quando i vari Twitter, Spotify, Netflix e Airbnb sono stati irraggiungibili per alcune ore.
 Fonte foto: web
Fonte foto: web
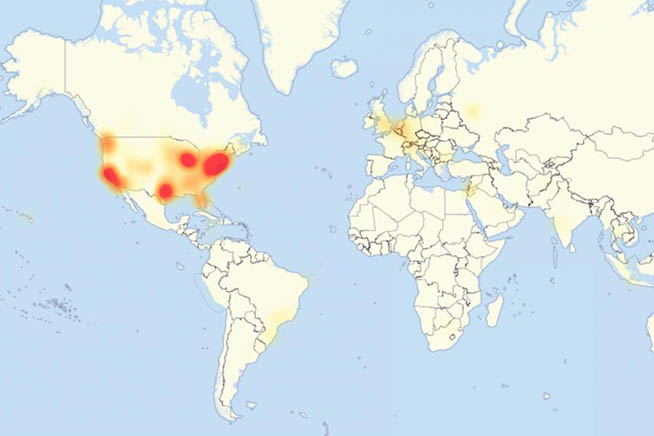
Le zone più colpite dall’attacco hacker DDoS del 21 ottobre scorso
Il pericolo IoT
Non è la prima volta che gli hacker ricorrono a immense botnet per sferrare attacchi DDoS contro obiettivi più o meno sensibili. L’attacco hacker del 21 ottobre, però, mostra una nuova e preoccupante tendenza: il sempre maggior ricorso a dispositivi connessi alla rete e appartenenti all’Internet of Things. Nell’attacco hacker del 21 ottobre sono stati utilizzati videocamere IP e videoregistratori digitali (DVR) della cinese XiongMai Technologies, ma non è da escludere che la prossima volta possano essere coinvolti altri dispositivi (elettrodomestici e termostati, tanto per fare due esempi) di altri produttori.

Videocamera di sicurezza IP
Telnet e DNS
E dire che l’attacco DDoS poteva essere evitato senza grossi problemi. Telnet, la funzione che consente di controllare i dispositivi a distanza, era stato disattivato con un aggiornamento firmware nel settembre 2015: sarebbe stato sufficiente un aggiornamento dei vari dispositivi, insomma, per ridurre la “potenza di fuoco” dei pirati informatici. È stata una falla di Telnet, infatti, a permettere agli hacker di entrare in possesso delle credenziali di accesso dei dispositivi IoT, rimpolpando così le fila della botnet.
 Fonte foto: Shutterstock
Fonte foto: Shutterstock
Server web
Un altro colpevole è sicuramente la fragilità del Domain Name System, e in particolare del TTL (acronimo di Time to Live). The DNS, in fact, doesn't always resolve the address following the same procedure (that is, it doesn't translate the IP in URL always accessing the same "address book"), but it can resort to "neighboring" servers that in the recent past have already opened the same address. If this happens, in fact, the information is kept in memory for a certain amount of time (the Time to Live), so as to speed up the resolution of the same address for other users. The combination of short TTL and lack of redundant servers actually amplified the scope of the October 21 attack: if the Time to Live of the various portals had been longer, in fact, it is likely that users would have been able to reach the requested sites anyway and the effects of the attack mitigated more quickly.
